This how-to article does not cover how to set up ADFS as an IdP. We assume you already have Active Directory setup and working with a table of users
Add a new Relying Party Trust in AD FS
-
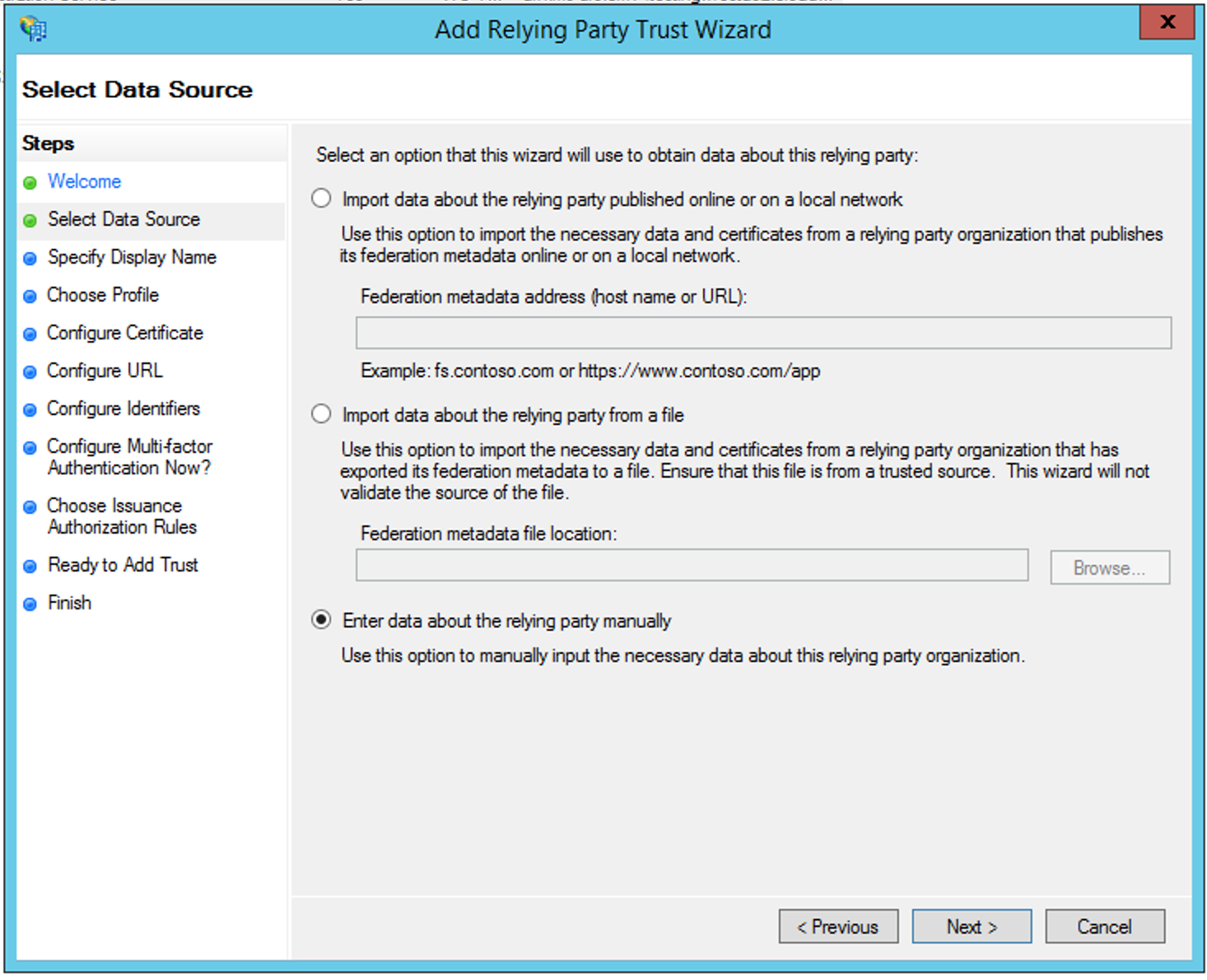
Open the Add Relying Party Trust Wizard
-
Click Start
-
Select Enter data about the relying party manually
-
Click Next >
-
Enter a Display Name
-
Click Next >
-
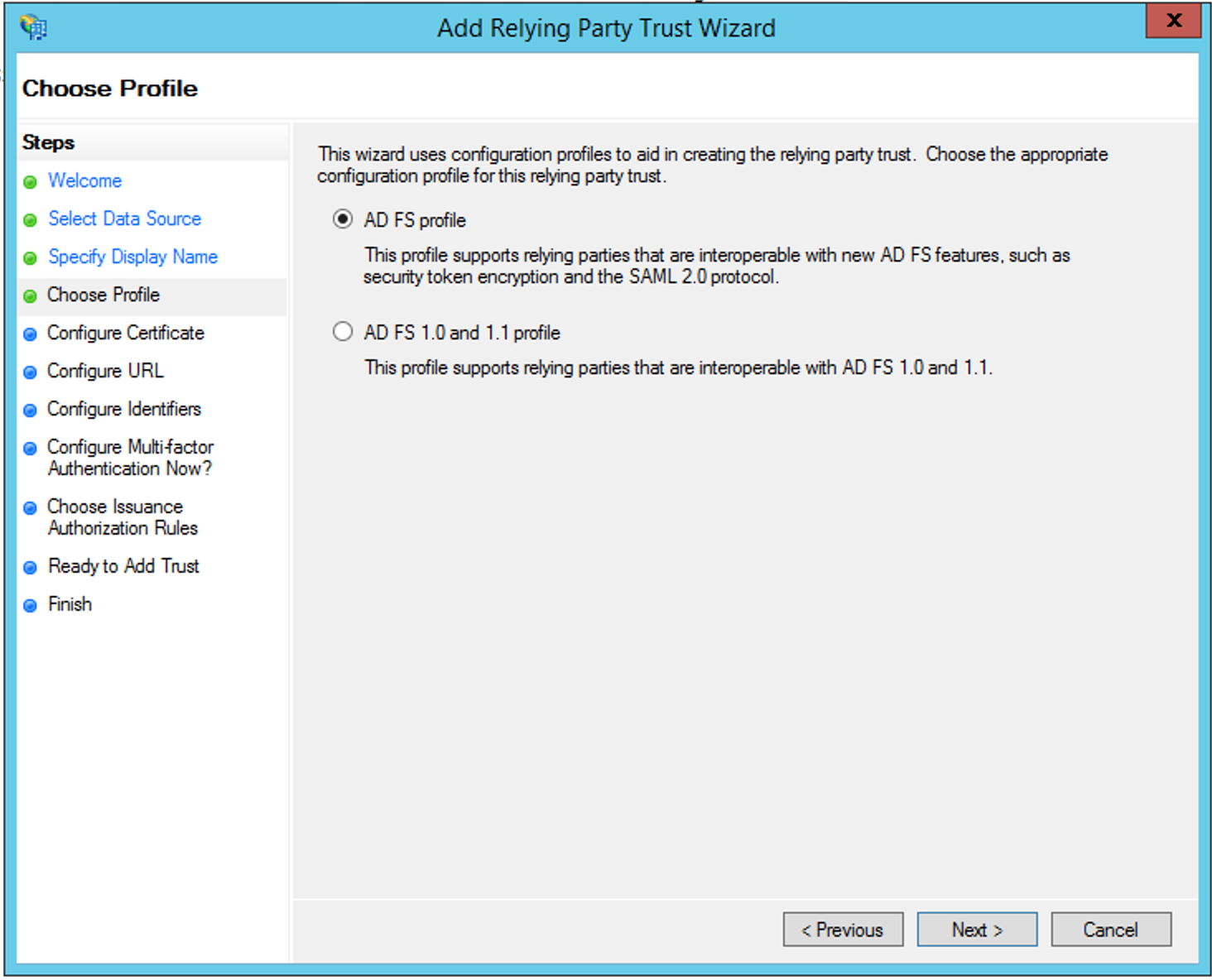
Leave configuration as AD FS profile
-
Click Next >
Open the Add Relying Party Trust Wizard
Click Start
Select Enter data about the relying party manually
Click Next >
Enter a Display Name
Click Next >
Leave configuration as AD FS profile
Click Next >
Create new Identity Provider in Social Pinpoint (new tab)
-
Navigate to Manage Account (/admin/manage)
-
Click the New Identity Provider (IdP) button in the top-right
-
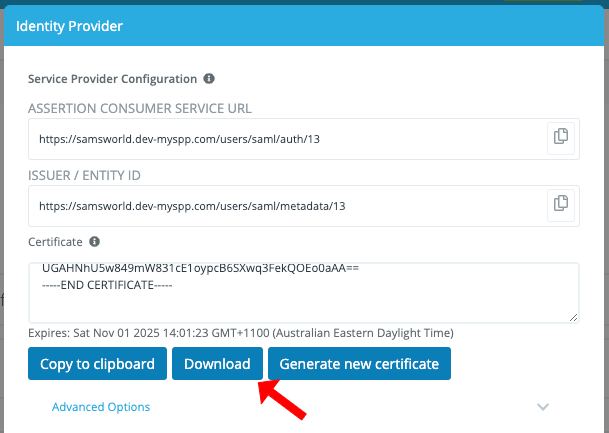
Under Certificate click Download - you will supply this certificate to AD FS
-
Save the value for ASSERTION CONSUMER SERVICE URL for later use
-
Save the value for ISSUER/ENTITY ID for later use
Navigate to Manage Account (/admin/manage)
Click the New Identity Provider (IdP) button in the top-right
Under Certificate click Download - you will supply this certificate to AD FS
Save the value for ASSERTION CONSUMER SERVICE URL for later use
Save the value for ISSUER/ENTITY ID for later use
Finish setup of Relying Party Trust in AD FS
-
Upload the certificate you obtained in the previous step by click Browse
-
Click Next >
-
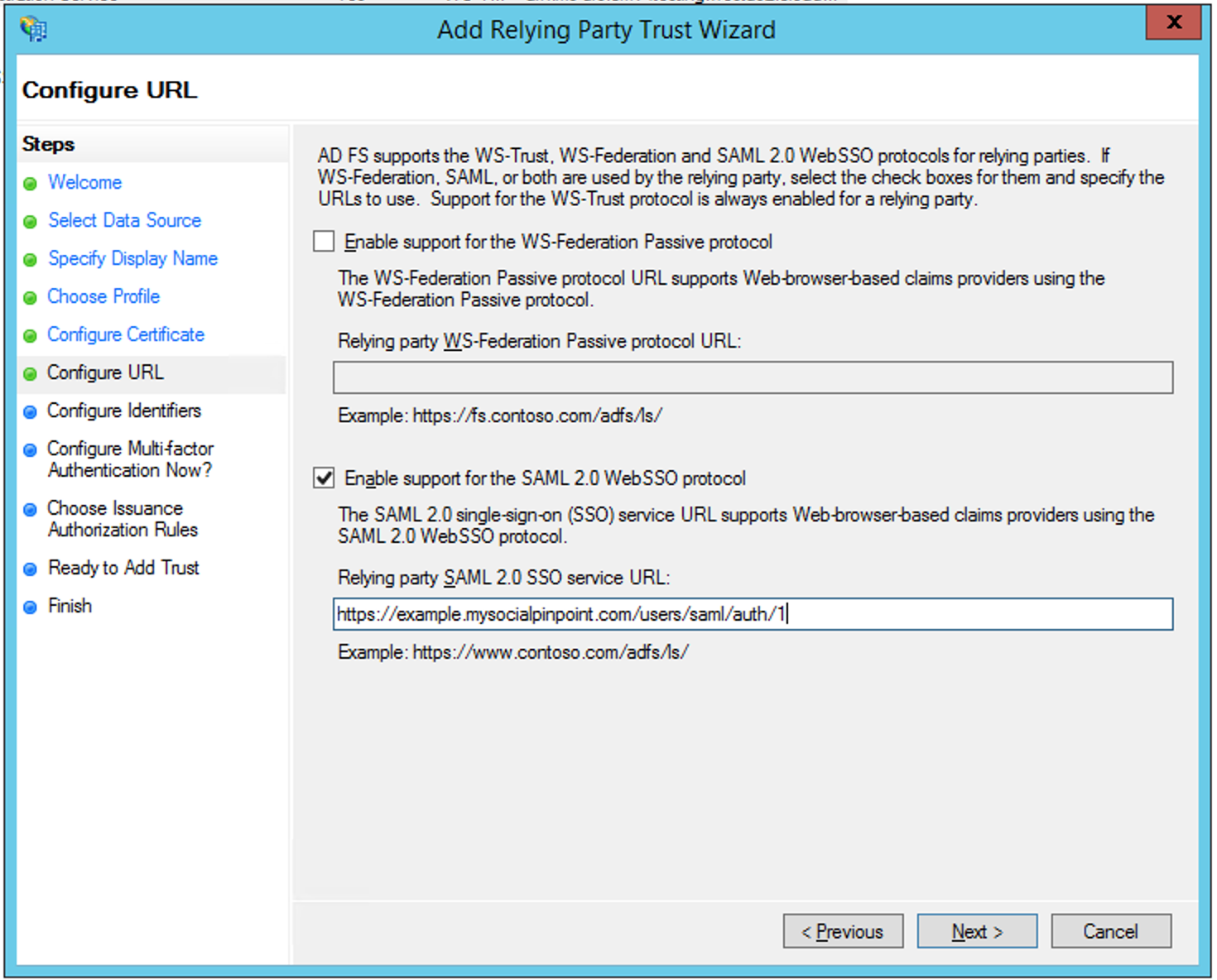
Check Enable support for the SAML 2.0 WebSSO protocol
-
In the text field, enter the value you saved for ASSERTION CONSUMER SERVICE URL
-
Click Next >
-
Enter the value you saved for ISSUER/ENTITY ID in the text field for Relying party trust identifier and click Add
-
Click Next >
-
Skip the next step - leave it as I do not want to configure multi-factor authentication settings for this relying party trust at this time and click Next >
-
Select the appropriate setting for Choose Issuance and click Next >
-
Double check your settings and click Next > if everything is okay
-
Select Open the Edit Claim Rules dialog for this relying party trust when the wizard closes and click Close
Upload the certificate you obtained in the previous step by click Browse
Click Next >
Check Enable support for the SAML 2.0 WebSSO protocol
In the text field, enter the value you saved for ASSERTION CONSUMER SERVICE URL
Click Next >
Enter the value you saved for ISSUER/ENTITY ID in the text field for Relying party trust identifier and click Add
Click Next >
Skip the next step - leave it as I do not want to configure multi-factor authentication settings for this relying party trust at this time and click Next >
Select the appropriate setting for Choose Issuance and click Next >
Double check your settings and click Next > if everything is okay
Select Open the Edit Claim Rules dialog for this relying party trust when the wizard closes and click Close
Set up Claim Rules
-
Click Add Rule…
-
Set Claim rule template as Send LDAP Attributes as Claims
-
Click Next >
-
Set Attribute store as Active Directory
-
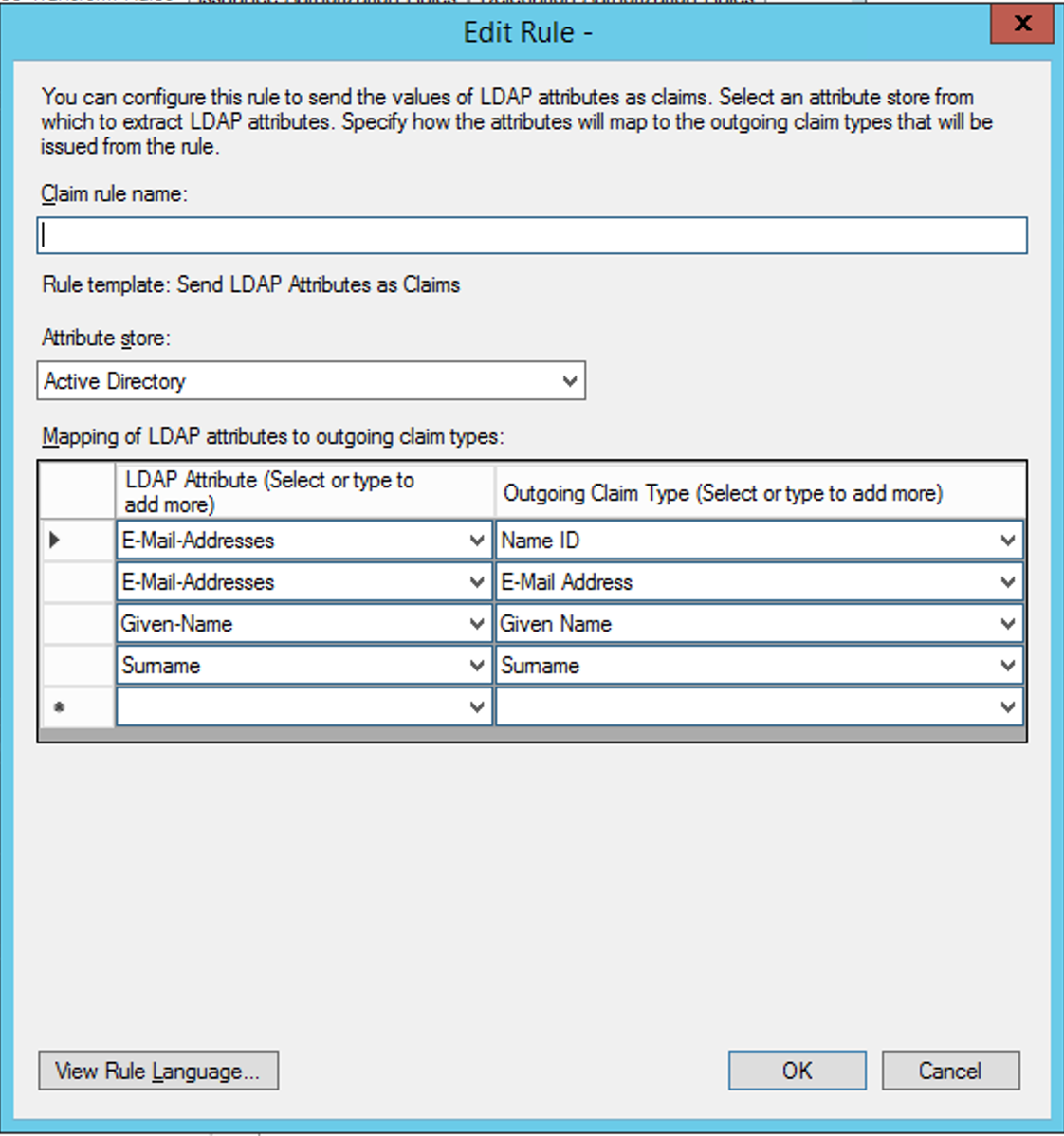
Create a rule that maps E-Mail-Addresses to Name ID
-
Create a rule that maps E-Mail-Addresses to E-Mail Address
-
Create a rule that maps Given-Name to Given Name
-
Create a rule that maps Surname to Surname
-
Set an optional Claim rule name if you wish
-
Click Finish
Click Add Rule…
Set Claim rule template as Send LDAP Attributes as Claims
Click Next >
Set Attribute store as Active Directory
Create a rule that maps E-Mail-Addresses to Name ID
Create a rule that maps E-Mail-Addresses to E-Mail Address
Create a rule that maps Given-Name to Given Name
Create a rule that maps Surname to Surname
Set an optional Claim rule name if you wish
Click Finish
Your Claim Rule should look like this before you finish
Finish setting up Identity Provider in Social Pinpoint
Extract the following information from AD FS:
-
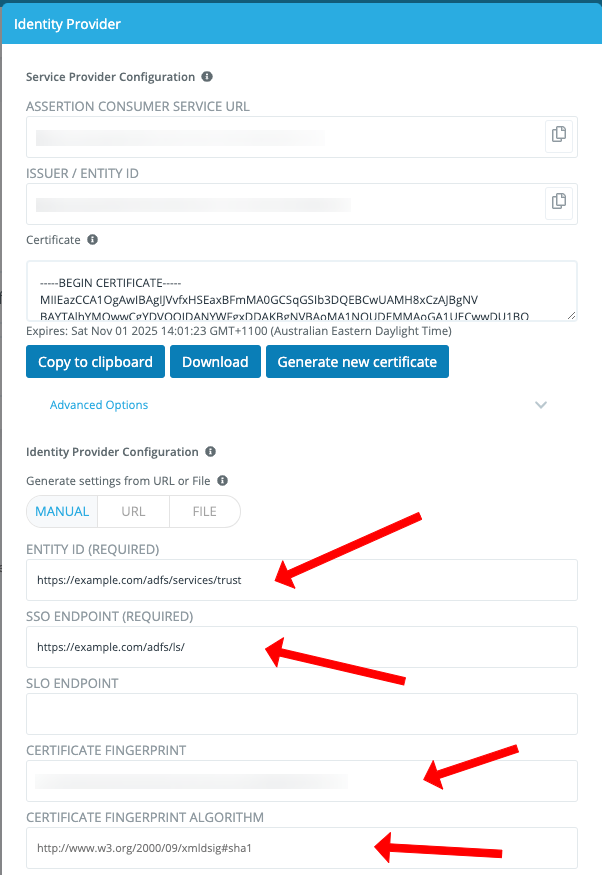
Entity ID (usually something like /adfs/services/trust)
-
Sign On URL (usually something like /adfs/ls/)
-
Certificate fingerprint
-
Certificate fingerprint algorithm
Entity ID (usually something like /adfs/services/trust)
Sign On URL (usually something like /adfs/ls/)
Certificate fingerprint
Certificate fingerprint algorithm
Enter these values into the following fields in Social Pinpoint
-
ENTITY ID
-
SSO ENDPOINT
-
CERTIFICATE FINGERPRINT
-
CERTIFICATE FINGERPRINT ALGORITHM
ENTITY ID
SSO ENDPOINT
CERTIFICATE FINGERPRINT
CERTIFICATE FINGERPRINT ALGORITHM
Set up Attribute Mapping in Social Pinpoint
-
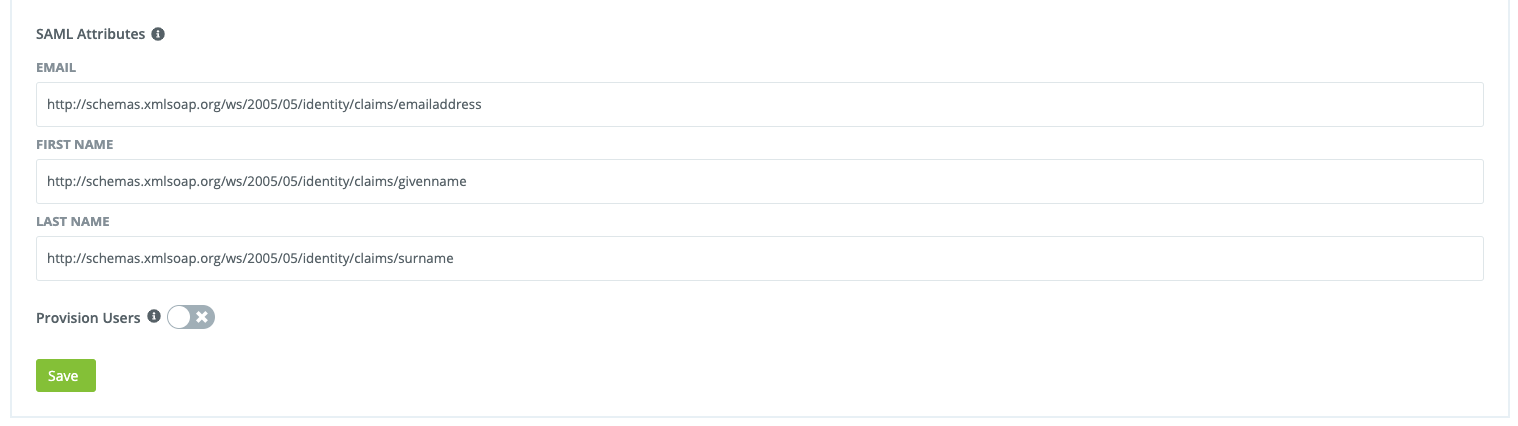
Set Email field to http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress
-
Set First Name field to http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname
-
Set Last Name field to http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname
-
Click Save
Set Email field to http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress
Set First Name field to http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname
Set Last Name field to http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname
Click Save
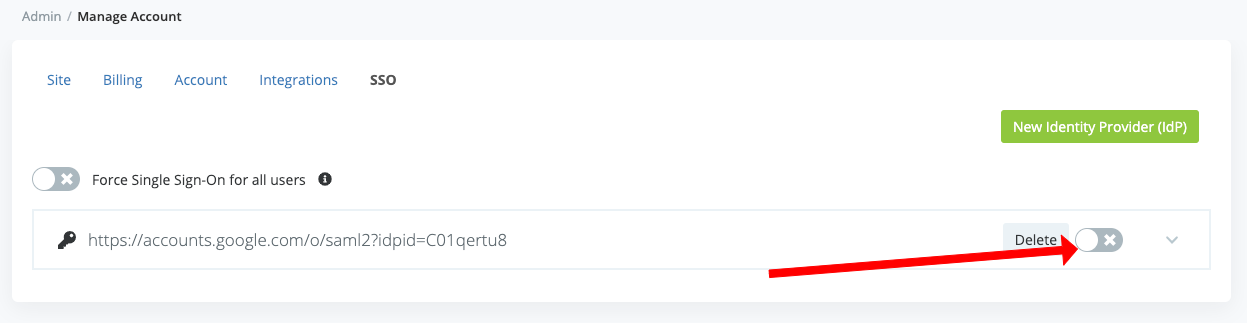
Enable the Identity Provider
Once you are happy with your settings you may enable your Identity Provider inside of Social Pinpoint.
Once enabled the a Single Sign-On button should appear on the sigh-in screen