This how-to article does not cover how to set up Google Admin as an IdP. We assume you already have Google Admin setup and working with a table of users
Create a new SAML app in the Google Admin console
-
Navigate to Apps > SAML Apps
-
Click Add at the bottom-right
-
Click SETUP MY OWN CUSTOM APP
-
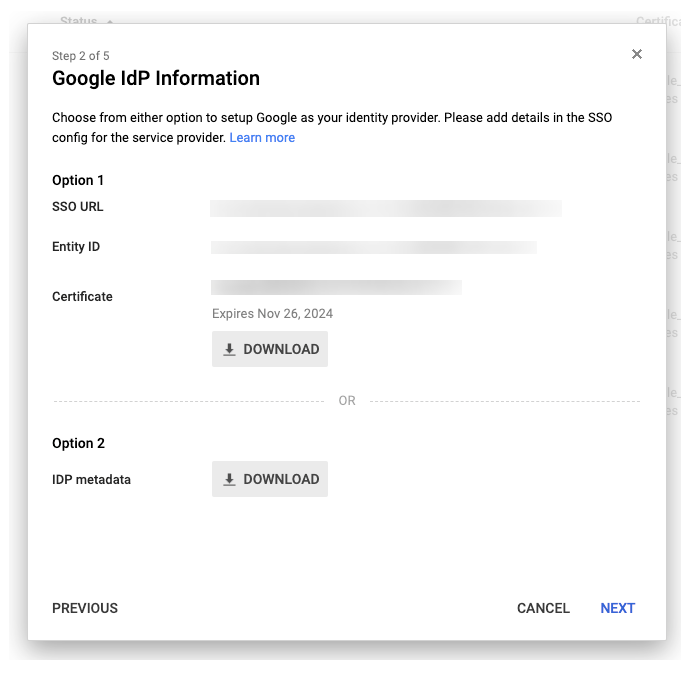
You should now see the Google Idp Information window with your SSO URL, Entity ID, and Certificate
-
DOWNLOAD the IDP metadata from Option 2
Navigate to Apps > SAML Apps
Click Add at the bottom-right
Click SETUP MY OWN CUSTOM APP
You should now see the Google Idp Information window with your SSO URL, Entity ID, and Certificate
DOWNLOAD the IDP metadata from Option 2
Create a new Identity Provider in Social Pinpoint (new tab)
-
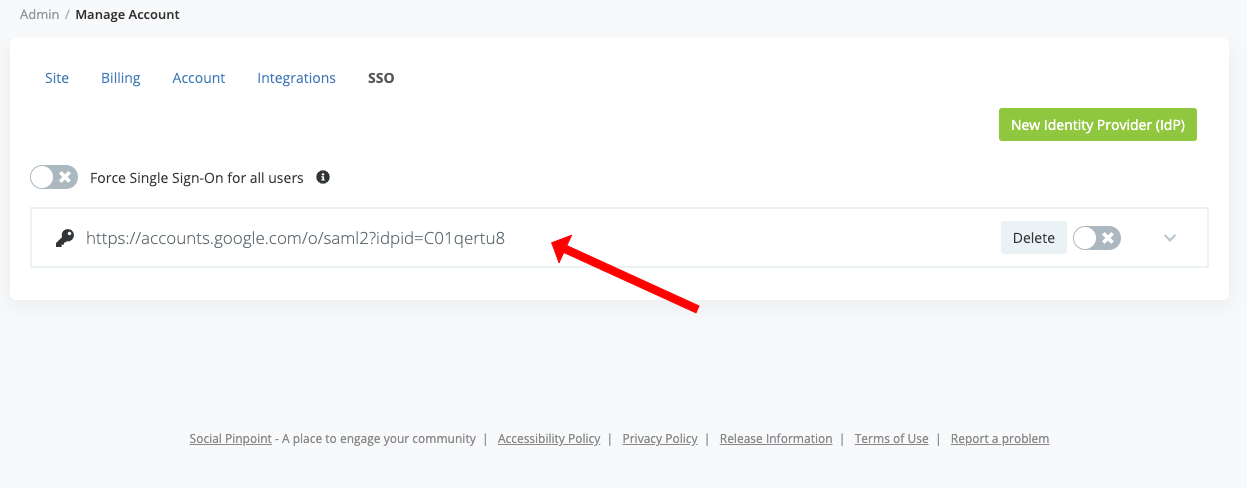
Navigate to Manage Account (/admin/manage)
-
Click the New Identity Provider (IdP) button in the top-right
-
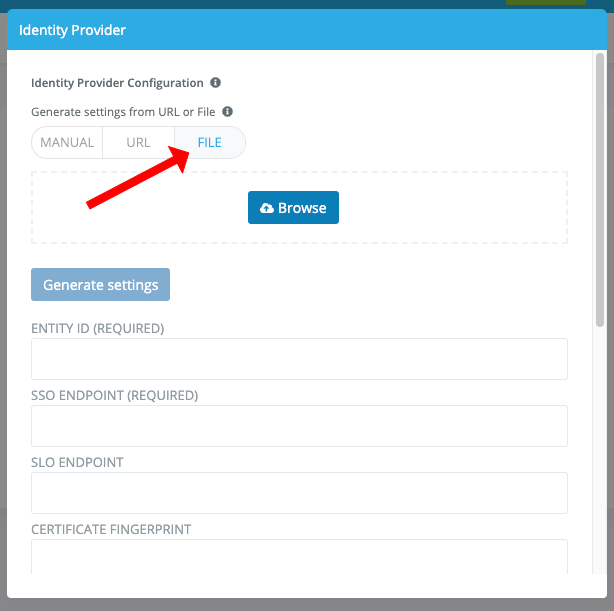
Navigate to the File button under Generate settings from URL or File
-
Upload the file that you received from Google in Step 5
-
Once the file has been uploaded click Generate Settings
-
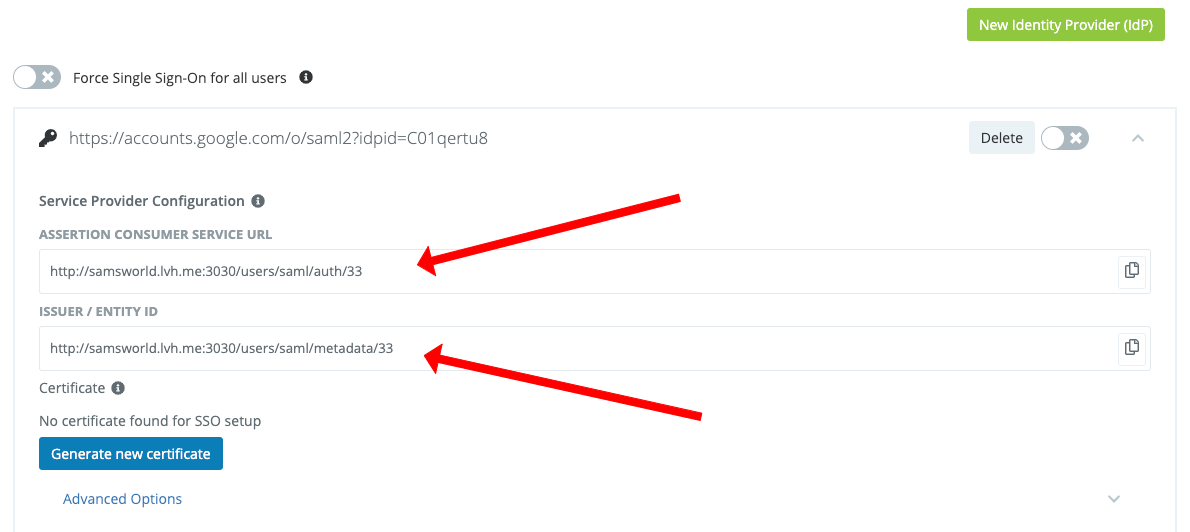
Open the Identity Provider you have just created and copy the ASSERTION CONSUMER SERVICE URL and ISSUER / ENTITY ID values
Navigate to Manage Account (/admin/manage)
Click the New Identity Provider (IdP) button in the top-right
Navigate to the File button under Generate settings from URL or File
Upload the file that you received from Google in Step 5
Once the file has been uploaded click Generate Settings
Open the Identity Provider you have just created and copy the ASSERTION CONSUMER SERVICE URL and ISSUER / ENTITY ID values
Finish setting up the Google SAML App
-
Back in Google Admin click NEXT and enter an Application Name. You may also enter a description and logo if you choose
-
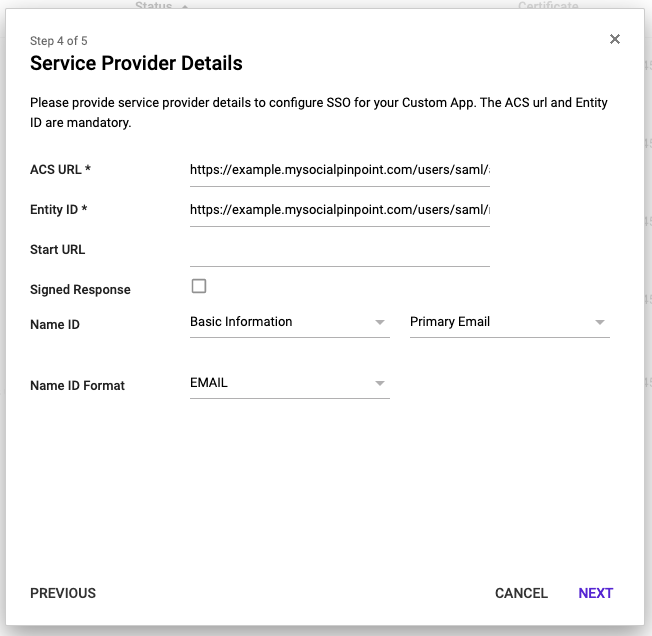
Enter the value you copied from ASSERTION CONSUMER SERVICE URL into the ACS URL field
-
Enter the value you copied from ISSUER / ENTITY ID into the Entity ID field
-
Make sure that Primary Email is being passed as the Name ID (see the screenshot for an example)
-
(Optional) Set a Name ID Format
-
Click Next
Back in Google Admin click NEXT and enter an Application Name. You may also enter a description and logo if you choose
Enter the value you copied from ASSERTION CONSUMER SERVICE URL into the ACS URL field
Enter the value you copied from ISSUER / ENTITY ID into the Entity ID field
Make sure that Primary Email is being passed as the Name ID (see the screenshot for an example)
(Optional) Set a Name ID Format
Click Next
Set up Attribute Mapping
This is required if you plan to allow the provisioning of Users. If so then you must at least provide a first name to be able to create a new User in Social Pinpoint
In Google Admin
-
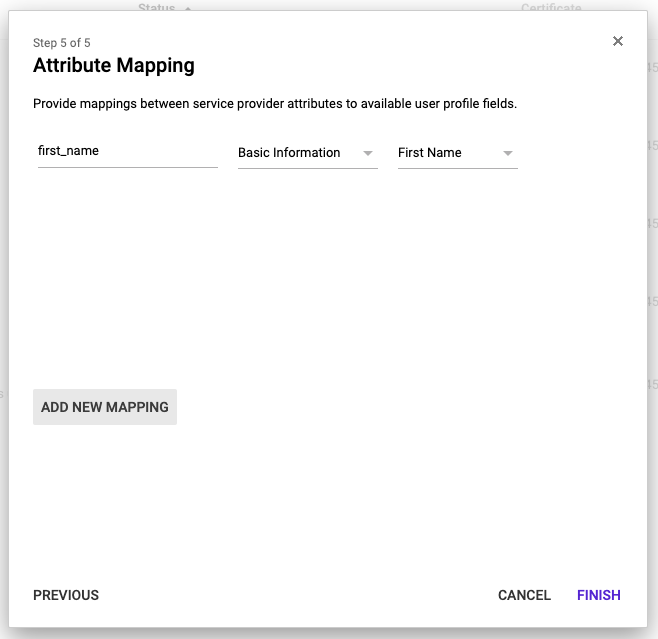
Click ADD NEW MAPPING
-
Set the name of the attribute as first_name
-
Using the other drop downs select the attribute you wish to pass as first_name (see screenshot for example)
-
Click FINISH
Click ADD NEW MAPPING
Set the name of the attribute as first_name
Using the other drop downs select the attribute you wish to pass as first_name (see screenshot for example)
Click FINISH
In Social Pinpoint
-
Open your Identity Provider and find the SAML Attributes section. Enter the value first_name in the appropriate fields (see screenshot for example)
Open your Identity Provider and find the SAML Attributes section. Enter the value first_name in the appropriate fields (see screenshot for example)
You may notice that there are 2 other attributes - email and last_name. You may enter these if you wish but they are not required
Enable the Identity Provider
Once you are happy with your settings you may enable your Identity Provider inside of Social Pinpoint.
Once enabled the a Single Sign-On button should appear on the sigh-in screen