This how-to article does not cover how to set up Okta as an IdP. We assume you already have Okta setup and working with a table of users.
Create a new SAML Application in Okta
-
From the Okta Admin console go to Applications > Applications (https://yoursubdomain.okta.com/admin/apps/active)
-
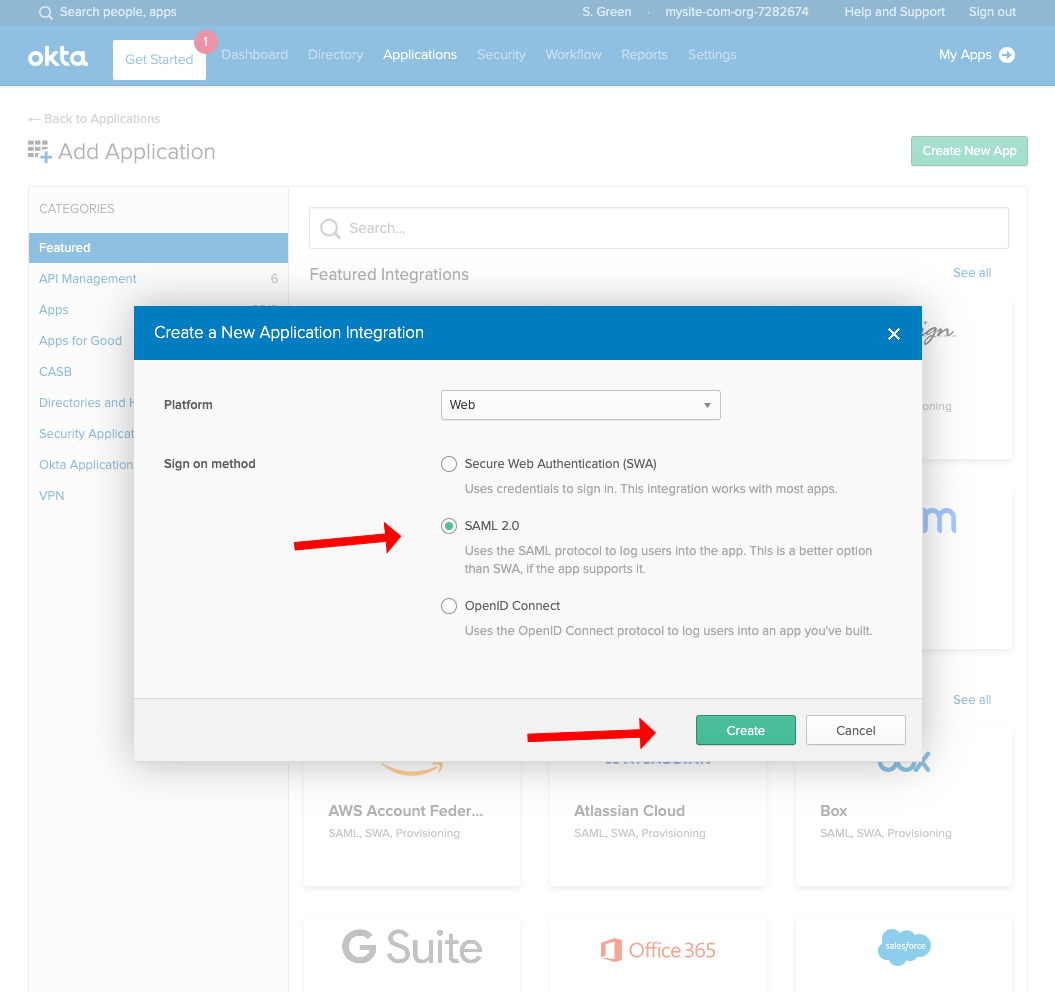
Click the Add Application button in the top-left
-
Click the Create New App button in the top-right
-
Select SAML 2.0 for the Sign on method
From the Okta Admin console go to Applications > Applications (https://yoursubdomain.okta.com/admin/apps/active)
Click the Add Application button in the top-left
Click the Create New App button in the top-right
Select SAML 2.0 for the Sign on method
Create a new Identity Provider in Social Pinpoint (new tab)
-
Navigate to Manage Account (/admin/manage)
-
Click the New Identity Provider (IdP) button in the top-right
-
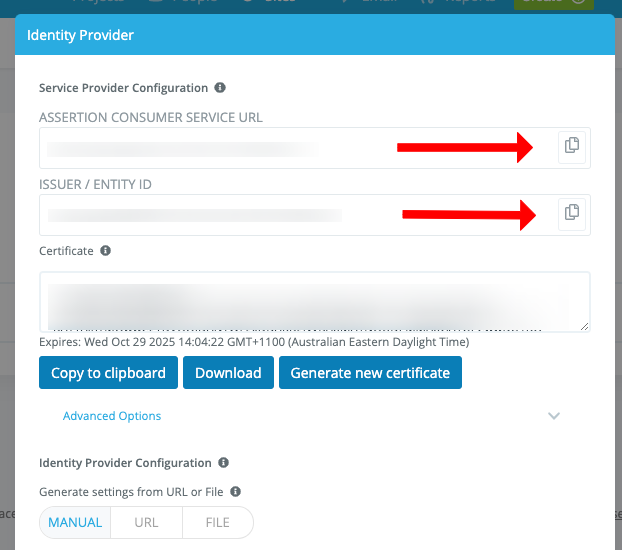
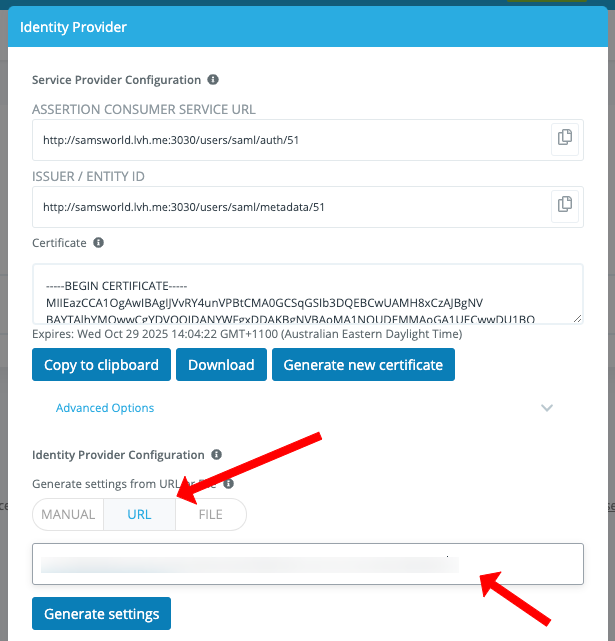
Copy the values for ASSERTION CONSUMER SERVICE URL and ISSUER / ENTITY ID and save these for the next step
-
Leave this window open for the moment
Navigate to Manage Account (/admin/manage)
Click the New Identity Provider (IdP) button in the top-right
Copy the values for ASSERTION CONSUMER SERVICE URL and ISSUER / ENTITY ID and save these for the next step
Leave this window open for the moment
Create SAML Integration (back in Okta)
-
Enter an App name
-
Click Next
-
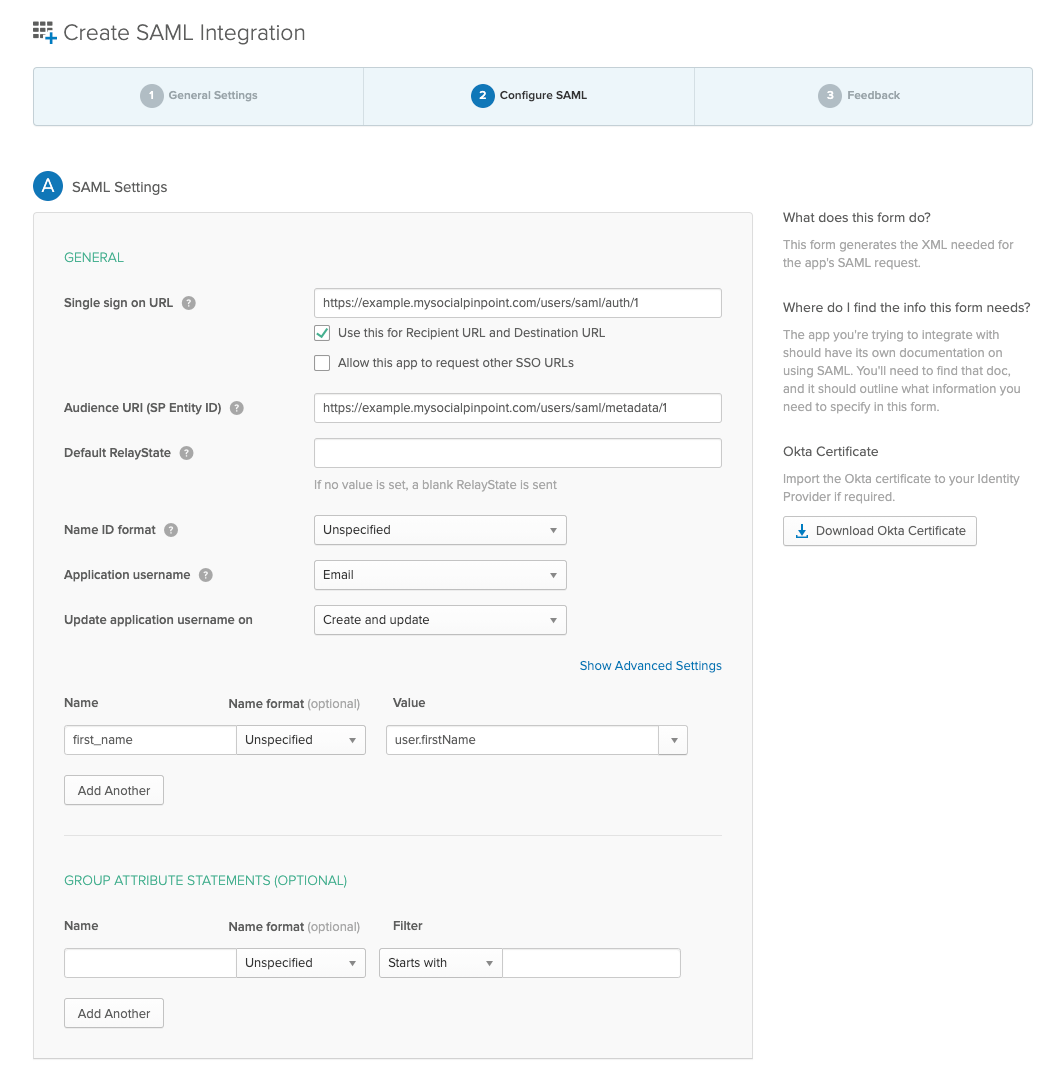
Enter the value you saved for ASSERTION CONSUMER SERVICE URL in the Single sign on URL field
-
Enter the value you saved for ISSUER / ENTITY ID in the Audience URI (SP Entity ID) field
-
For the Application username field select email
-
Add an attribute called first_name with Name format Unspecified and value user.firstName (see screenshot for example setup) (only required if you wish to provision users)
-
Click the Next button
-
Continue until your app has been created
-
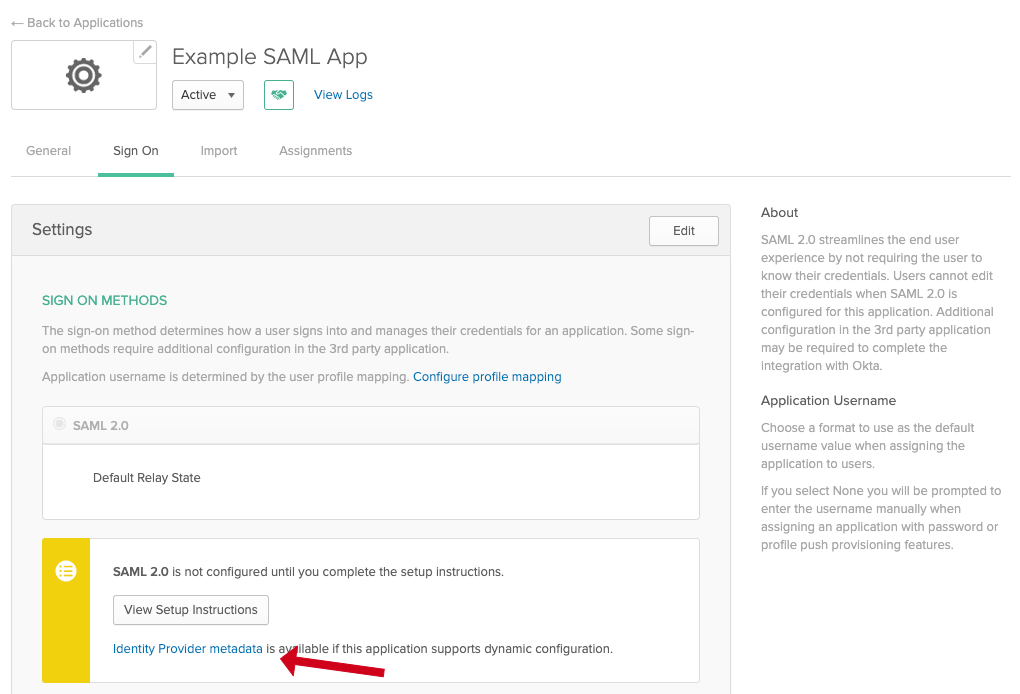
Navigate to the Sign On tab and copy the link value for the link Identity Provider metadata (see screenshot for location of link)
Enter an App name
Click Next
Enter the value you saved for ASSERTION CONSUMER SERVICE URL in the Single sign on URL field
Enter the value you saved for ISSUER / ENTITY ID in the Audience URI (SP Entity ID) field
For the Application username field select email
Add an attribute called first_name with Name format Unspecified and value user.firstName (see screenshot for example setup) (only required if you wish to provision users)
Click the Next button
Continue until your app has been created
Navigate to the Sign On tab and copy the link value for the link Identity Provider metadata (see screenshot for location of link)
Enter metadata url in Social Pinpoint
-
Under the Identity Provider Configuration section select URL from the tab options
-
Paste the metadata url you got from the previous step and click Generate settings
Under the Identity Provider Configuration section select URL from the tab options
Paste the metadata url you got from the previous step and click Generate settings
(Optional) Set up attribute mapping
If you wish to provision users then you must at least provider first name from the IdP to SPP
-
Navigate to the FIRST NAME field under SAML Attributes and enter the value first_name (to match the value you entered in Okta)
-
Click Save in the bottom-left
Navigate to the FIRST NAME field under SAML Attributes and enter the value first_name (to match the value you entered in Okta)
Click Save in the bottom-left
Enable the Identity Provider
Once you are happy with your settings you may enable your Identity Provider inside of Social Pinpoint.
Once enabled the a Single Sign-On button should appear on the sigh-in screen
Once you have assigned your users to this app then they will be able to sign in to Social Pinpoint with one-click
-1.png)
